This article includes:
- Background on why you might need to deal with IPv6 tunneling (basically when your ISP sucks)
- Prerequisites for adding your own home IPv6 service
- Setting up IPv6 with DD-WRT (and a Linksys/Cisco E3000)
- Setting up IPv6 with a Cisco 1811/1811W
- Setting up IPv6 with a Cisco 1941W
Background
As I’m sure many are, I’m stuck with not many options for high speed broadband service; just two options for my neighborhood so I went with the lesser evil, Verizon FiOS. FiOS is their fiber service. It’s actually pretty decent from a speed and stability perspective, if we’re talking IPv4, but thus far their IPv6 is non-existent. They’ve been giving empty promises of it ‘coming soon’ for years now and there’s nothing to show for it other than some brief rumors in 2012 that they were testing it in some employees’ homes. The rumor is that they’re not pushing very hard to get it done because it would mean swapping out a LOT of shitty ActionTec modems since they ones they deployed for years were not IPv6 capable. Their 4G LTE cell network has great IPv6 so they have knowledge in-house, so that makes me think the equipment swap/cost factor may be the real issue. So, what to do? Get an IPv6 tunnel via Hurricane Electric’s Tunnel Broker service, and then hook your home router/modem into it. Your IPv4 traffic will flow like normal, your IPv6 traffic will traverse a 6in4 tunnel to Hurricane Electric where it will then go on its way like any other routed traffic across the internet. This service is provided by them for FREE! You will need some new hardware for your house most likely, but perhaps you can get by with what you already have. Four options I’d recommend depending on how feature-rich of a solution you’d like:
- First, perhaps your existing home router/modem can be put to good use. What you’re going to need is a router compatible with DD-WRT; a free linux-based OS specifically designed to go on consumer cable and DSL modem hardware. There are a few things though; your router must meet the following requirements:
- Support running a DD-WRT “standard” image. The “mini” images are not compatible with IPv6.
- Have at least a 6+ MB flash but preferably 8 MB or better. The standard image no longer leaves enough room on a 4 MB flash to have a jffs filesystem added, which you need for this project. Alternatively; if your router has USB ports, you may be able to use a flash drive with it and get around this issue even if it’s a 4 MB router.
- Support at least DD-WRT v24-sp2 or newer.
- If your router doesn’t meet these requirements, buy the E3000 mentioned next. It’s a great wireless-N router that can be found really inexpensively, 8 MB flash, 64 MB memory.
- Next, the super cheap option. Buy a Linksys (now Cisco) E3000 router on eBay; you can typically find them in the $40 range. They meet all of the above requirements for DD-WRT.
- Third; a bit more expensive but with more functionality: buy a Cisco 1811 router on eBay. You can typically find those in the <$150 range. The big caveat; you can’t do IPv6 on an 1811’s wireless, so you’ll need a second wireless device to act as a bridge anyway, which means don’t waste your money on the wireless-enabled version of the 1811, get the wired-only model. In fact, you can even use the previously mentioned E3000 with DD-WRT on it as your wifi bridge.
- Fourth; a LOT more expensive, Cisco 1941W router. Gets you basically the same thing the 1811 gets you but with native IPv6 wifi support included, support for later Cisco IOS images, better VPN throughput if you do site to site VPN’s on the device, better performance if you load it up with access lists, etc.. You’ll be spending probably $800+ for one of these used, so not really worth it for most people but some will find it useful, especially if you’re trying to get IPv6 service at a branch office or something similar.
Pre-Req’s
Sign up for a Tunnel Broker account at http://www.tunnelbroker.net/ They’ll issue you a specific IPv6 allocation, actually up to five if you need to deploy in more than one location, and they’ll guide you through picking one of their end points to tunnel your traffic to; you can choose based on performance and/or geography. Note this information because you’ll need it for any of the following parts. For network admins, they’ll also issue you a /48 if you request it and want to have multiple IPv6 routed networks behind your tunnel router. If you have any devices on your network that will be talking IPv6 and do not support path MTU discovery (very rare), set their MTU to 1480 since that’s the largest unfragmented packet size you can send through the 6to4 tunnel and they’d go with a lower MTU if allowed to do things themselves.
Linksys E3000 or your own DD-WRT-compatible router
This is a great starter option that will get you IPv6 service on your home network. They’re cheap and reliable. I’m currently using one of these running “DD-WRT v24-sp2 (04/13/11) std-usb-nas (SVN revision 16785)”. The instructions for installing DD-WRT on your E3000 can be found at http://www.dd-wrt.com/wiki/index.php/Linksys_E3000 Walking you through that is a bit beyond the scope of this article but as long as you’re careful and can follow directions, you should be able to make it through without destroying your router. Keep in mind that if you do not follow those directions precisely, you stand a good chance of rendering your router unbootable and worthless, so have someone else do it if that sounds like a risk you don’t want to take. Now with your IPv6 allocation and your router running DD-WRT, you’re ready for the next step; enabling it for IPv6 tunneling. There’s a howto on the DD-WRT site at http://www.dd-wrt.com/wiki/index.php/IPv6#Hurricane_Electric.27s_Tunnelbroker.net but it has some errors and is not the easiest thing to follow. I’ll run you through my settings; keep in mind these are specific to my version of DD-WRT so some versions may be different:
- Under Setup -> VLANs I have ports 1,2,3 and 4 set to VLAN 1 and “assigned to bridge” LAN. VLAN 2 is assigned to the “W” port, i.e. WAN. Down at the bottom I have wireless set to LAN. This is important because it means it’s going to bridge your Wifi and wired LAN so both use the same addresses and devices on each can talk to each other without routing.
- I think this is done automatically by the above setup but on Setup -> Networking I have a bridge zero defined, name br0, STP Off, Prio 32768, MTU 1480 (since the largest tunneled IPv6 unfragmented packet size is 1480). Also on that page the bridging table display confirms that my bridge zero is bridging vlan 1, eth1 and eth2. The WAN port assignment on that page is showing vlan 2.
- Please make sure to set up proper wireless security settings; i.e. WPA2 w/AES and a strong pass phrase as a minimum.
- Under Administration -> Management, you’ll need to create a JFFS filesystem, here’s the steps:
-
- On the router web page click on Administration.
- Scroll down until you see JFFS2 Support section.
- Click Enable JFFS.
- Click Save.
- Wait a few seconds, then click Apply.
- Wait again. Go back to the Enable JFFS section, and enable Clean JFFS.
- Do not click “Save”. Click Apply instead.The router formats the available space.
- Wait till you get the web-GUI back, then disable “Clean JFFS” again.
- Click “Save”.
- It may be wise to Reboot the router, just to make sure it was done correctly and comes up as available afterward.
- Under Administration -> Management, I have all of the following set (not all of this has anything to do with IPv6, just running you through them all):
- Web access set to https only, info site enabled, mac masking enabled.
- All remote access methods disabled; this is referring to access from the public-facing side of the device, not access from internally.
- Boot Wait enabled.
- Cron enabled, but no jobs set.
- 802.1x disabled; I don’t use it.
- Reset button enabled.
- Routing enabled.
- IPv6 Support – enabled and Radvd enabled. In the Radvd config box, input the following:
-
interface br0 { MinRtrAdvInterval 3; MaxRtrAdvInterval 10; AdvLinkMTU 1480; AdvSendAdvert on; prefix 2001:470::/64 { AdvOnLink on; AdvAutonomous on; AdvValidLifetime 86400; AdvPreferredLifetime 86400; # Base6to4Interface vlan2; }; }; - The parts of the above you will need to modify are highlighted red; 1480 is the MTU for my LAN because tunneled packets would get fragmented if it’s left to 1500. Most devices do path MTU discovery so you won’t have to do anything further on your actual devices. The IPv6 protocol actually requires IPv6-enabled systems to do path MTU discovery, or if they’re not capable of doing it, to revert to a size of 1280. The prefix value comes from Tunnel Broker when you sign up and are issued an allocation specific to you.
- JFFS2 enabled, clean JFF2 disabled. On my E3000 I end up with 2.2 MB available for JFFS.
- CIFS disabled.
- Under Administration -> Commands I have the following setup for the “Startup” config:
-
#Enable IPV6 insmod /lib/modules/`uname -r`/kernel/net/ipv6/sit.ko sleep 5 radvd -C /tmp/radvd.conf start sleep 5 rm -f /tmp/wanip /jffs/updateipv6.sh 2> /jffs/startup.debug kill -HUP $(cat /var/run/radvd.pid) sleep 10 echo "starting radvd" >> /jffs/startup.debug radvd -C /jffs/radvd.conf start &
-
- Next, you’re going to need to SSH into your router. If you don’t have an SSH client, try putty. Just ssh as root to the router’s default gateway IP that your computer is using. Once logged in, paste the following AFTER you make edits to the first five lines to contain your proper Tunnel Broker credentials and information provided by them:
cat > /jffs/updateipv6.sh <<'FEOF'
#!/bin/sh -x
USERID="my_tunnelbroker_user_id"
PASSWORD="my_tunnelbroker_password"
TUNNEL_ID="tunnelbroker_id_123456"
CLIENT_IPV6_ADDRESS="tunnelbroker_ipv6_allocation_2001:470::/64"
SERVER_IPV4_ADDRESS="tunnelbroker_server_ip"
echo >> /tmp/wanip
WANIP_OLD=`cat /tmp/wanip`
WANIP=$(ip -4 addr show dev vlan2 | grep 'inet ' | awk '{print $2}' | cut -d/ -f1)
if [ -n "$WANIP" ]
then
if [ "$WANIP" != "$WANIP_OLD" ]
then
echo "External IP: $WANIP" 1>&2
ROUTED_ADDRESS=`sed -n -e 's,^ *prefix *\([^ ]*\) *{,\1,p' /tmp/radvd.conf`
if [ $ROUTED_ADDRESS = "0:0:0:1::/64" ]
then
CLIENT_IPV6_ADDRESS=""
fi
ip tunnel del tun6to4 2>>/dev/null
ip tunnel del he-ipv6 2>>/dev/null
if [ -n "$CLIENT_IPV6_ADDRESS" ]
then
echo "Configure he-ipv6 tunnel" 1>&2
MD5PASSWORD=`echo -n "$PASSWORD"|md5sum|sed -e 's/ *-//g'`
/usr/bin/wget 'http://ipv4.tunnelbroker.net/ipv4_end.php?ipv4b='AUTO'&pass='$MD5PASSWORD'&user_id='$USERID'&tunnel_id='$TUNNEL_ID -O - exit
ip tunnel add he-ipv6 mode sit ttl 255 remote $SERVER_IPV4_ADDRESS local $WANIP
ip link set he-ipv6 up
ip addr add $CLIENT_IPV6_ADDRESS dev he-ipv6
ip route add ::/0 dev he-ipv6
BR0_MAC=$(ifconfig br0 |sed -n -e 's,.*HWaddr \(..\):\(..\):\(..\):\(..\):\(..\):\(..\).*,\1\2:\3\4:\5\6,p')
# These commands aren't on HE's website, but they're necessary for the tunnel to work
ip -6 addr add $(echo "$ROUTED_ADDRESS"|sed "s,::/..,::$BR0_MAC/64,") dev br0
ip -6 route add 2000::/3 dev he-ipv6
else
echo "Configure tun6to4 tunnel" 1>&2
V6PREFIX=$(printf '2002:%02x%02x:%02x%02x' $(echo $WANIP | tr . ' '))
ip tunnel add tun6to4 mode sit ttl 255 remote any local $WANIP
ip link set tun6to4 mtu 1480
ip link set tun6to4 up
ip -6 addr add $V6PREFIX:0::1/16 dev tun6to4
ip -6 addr add $V6PREFIX:1::1/64 dev br0
ip -6 route add 2000::/3 via ::192.88.99.1 dev tun6to4
fi
echo 1 > /proc/sys/net/ipv6/conf/all/forwarding
fi
fi
FEOF
chmod 755 /jffs/updateipv6.sh
Okay, with all that completed, reboot your router and you should be IPv6-enabled with a tunnel through Hurrican Electric. Your computer *should* hear the router advertisement from your IPv6-enabled DD-WRT router and assign itself an IPv6 address via stateless autoconfig so assuming your computer is IPv6-enabled and has it on, just visit http://test-ipv6.com/ and it should tell you what your IPv6 address is. If you use FireFox, there’s a cool plugin called IPvFox that will add a little number to the right end of your URL bar that will indicate 6 or 4 if the site is using one or the other, or 6 or 4 followed by superscript and subscript to indicate if there is third party content on the page coming in via the other protocols. You can click the number to get a further breakdown on the usage. For example, on this site: 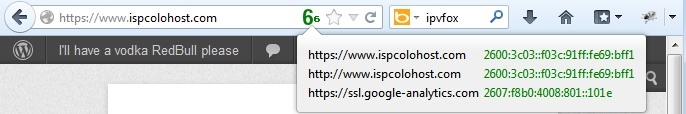
SECURITY TIME!
Now, before we wrap up, there’s one more important thing to keep in mind; this is a two way IPv6 tunnel; i.e. your home network is now exposed to the internet for IPv6 traffic. Yes, your home network does also currently have 18,446,744,073,709,551,616 (18 quintillion) unique IPv6 addresses, so the chances of a remote hacker guessing the right one where your computers reside is a lot lower, but they need to be protected none the less. Two ways to do this; either firewall at the router, or protect your internal computers with their own firewalls. Unfortunately DD-WRT does not come with the linux ipv6 firewall kernel module pre-built, so you need to download it from someone else or build it yourself. That goes beyond the scope of this article but you’ll find info on that here: http://www.dd-wrt.com/wiki/index.php/IPV6#ip6tables_for_K26_big_images If you do choose to build the kernel module, the commands you need to add to the startup scripts are quite simple: ip6tables -P INPUT DROP ip6tables -A INPUT -m state --state NEW,ESTABLISHED -j ACCEPT I personally chose to firewall at the host because some of my internal computers I want to be able to reach from the internet. On those, I block all but the services I need access to, keep them up to date on patches and, when possible, limit the IP’s that can connect to those services.
Cisco 1811 Router
This one is a far more robust option than the above DD-WRT-based solutions, and actually very easy to configure. These are very reliable routers and can often be found on eBay for cheap. The 1811 also has some encryption offload hardware that will make for pretty decent VPN throughput; more than enough to saturate any home office / remote office type bandwidth. If you buy one online, don’t waste money on the wireless version unless you don’t care about doing IPv6 on the wifi part of the box. From what I’ve been told, whether you run version 12.x or 15.x of IOS, you’re not going to get IPv6 support on the wireless radios either way. I can confirm that 12.x definitely does not work. Also, if you’re buying used, and you don’t have access to Cisco downloads, and you don’t know someone who does, try to get the seller to install the latest version before shipping it to you. Currently (summer 2013) I’m running 12.4(24)T8 which is the latest of the 12.4T series. Even though the Cisco validator tool suggests you need 256 MB memory and 64 MB flash, that image works fine on a 128/32 setup even with a bunch of services enabled. I’m running the advanced ip services image, not the enterprise image. So with that being said, let’s set up some IPv6. The first part is super easy because in the Hurricane Electric Tunnel Broker website, they’ll build the configuration for you. Just create a new network allocation, click into it, and then go to the Example Configuration tab and select Cisco IOS: 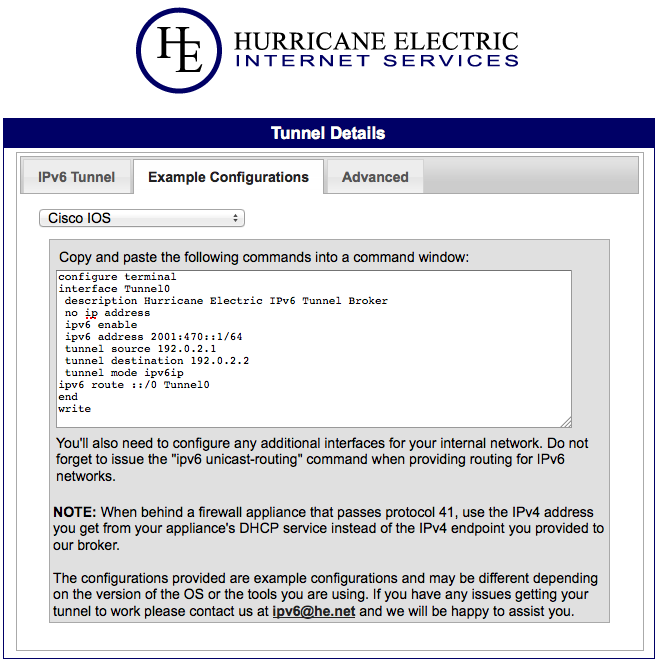 I’m going to go ahead and build you a complete config based on the above sample info from Tunnel Broker. This config is going to assume a typical home network setup with private IP’s and DHCP. I’m going to explain what everything is after the config and highlight things that MUST be changed in red, so please read through it first before connecting any cables or pasting into your router:
I’m going to go ahead and build you a complete config based on the above sample info from Tunnel Broker. This config is going to assume a typical home network setup with private IP’s and DHCP. I’m going to explain what everything is after the config and highlight things that MUST be changed in red, so please read through it first before connecting any cables or pasting into your router:
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec localtime
service password-encryption
!
hostname home-router-1
!
boot-start-marker
boot-end-marker
!
logging message-counter syslog
enable password MY_PASSWORD
!
aaa new-model
!
aaa session-id common
clock timezone EDT -5
clock summer-time EDT recurring
!
!
dot11 syslog
!
dot11 ssid MY_WIFI_SSID
authentication open
authentication key-management wpa
wpa-psk ascii MY_WIFI_PASSWORD
!
no ip source-route
!
!
ip dhcp excluded-address 192.168.0.1 192.168.0.10
ip dhcp excluded-address 192.168.1.1 192.168.1.10
!
ip dhcp pool WIRED
network 192.168.0.0 255.255.255.0
default-router 192.168.0.1
dns-server 8.8.8.8
!
ip dhcp pool WIFI
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
dns-server 8.8.8.8
!
ip cef
ip domain lookup source-interface Vlan100
ip name-server 8.8.8.8
ipv6 unicast-routing
no ipv6 source-route
ipv6 cef
!
multilink bundle-name authenticated
!
no spanning-tree optimize bpdu transmission
vtp mode transparent
username root password MY_PASSWORD
!
vlan 100 name OUTSIDE
!
vlan 101 name INSIDE
!
ip ssh time-out 60
ip ssh authentication-retries 2
ip ssh source-interface Vlan101
ip ssh logging events
ip ssh version 2
!
interface Tunnel0 description Hurricane Electric IPv6 Tunnel Broker
no ip address
ipv6 address 2001:470::2/64
ipv6 enable
ipv6 traffic-filter FirewallIPv6 in
tunnel source vlan 100
tunnel destination 10.0.0.1
tunnel mode ipv6ip
!
interface Dot11Radio0
ip address 192.168.1.1 255.255.255.0
ip access-group WIFI-Restrict in
ip nat inside ip virtual-reassembly
!
encryption mode ciphers aes-ccm
!
ssid MY_WIFI_SSID
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0 54.0
channel least-congested 2412 2442 2462
station-role root access-point
no cdp enable
!
interface Dot11Radio1
no ip address
shutdown
speed basic-6.0 9.0 basic-12.0 18.0 basic-24.0 36.0 48.0 54.0
station-role root
!
interface FastEthernet0
no ip address
shutdown
!
interface FastEthernet1
no ip address
shutdown
!
interface FastEthernet2
description ISP-OUTSIDE
switchport access vlan 100
!
interface FastEthernet3
description INSIDE
switchport access vlan 101
!
interface FastEthernet4
description INSIDE
switchport access vlan 101
!
interface FastEthernet5
description INSIDE
switchport access vlan 101
!
interface FastEthernet6
description INSIDE
switchport access vlan 101
!
interface FastEthernet7
description INSIDE
switchport access vlan 101
!
interface FastEthernet8
description INSIDE
switchport access vlan 101
!
interface FastEthernet9
description INSIDE
switchport access vlan 101
!
interface Vlan1
no ip address
shutdown
!
interface Vlan100
description Public Internet
ip address dhcp
ip access-group Firewall in
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat outside
ip virtual-reassembly
!
interface Vlan101
description INSIDE
no ip address
ipv6 address 2001:db8:1::1/64
ipv6 nd reachable-time 900000
ipv6 nd ns-interval 5000
ipv6 nd other-config-flag
ipv6 nd router-preference High
no ipv6 redirects
no ipv6 unreachables
!
interface Async1
no ip address
encapsulation slip
shutdown
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 dhcp
no ip http server
no ip http secure-server
!
!
ip nat inside source route-map No-NAT interface Vlan100 overload
!
ip access-list extended Firewall
remark # Permit DNS responses
permit udp any eq domain any gt 1023
remark # Allow return traffic from outbound TCP sessions
permit tcp any any established
remark # HE.net IPv6 Tunnel permit 41 host 10.0.0.1 any
deny ip any any
ip access-list extended INSIDE-No-NAT
permit ip 192.168.0.0 0.255.255.255 any
permit ip 192.168.1.0 0.255.255.255 any
ip access-list extended WIFI-Restrict
deny ip any 192.168.0.0 0.255.255.255
permit ip any any
!
access-list 10 remark NetMgmt
access-list 10 permit 192.168.0.0 0.255.255.255
access-list 10 deny any
!
ipv6 route ::/0 Tunnel0
!
route-map No-NAT
permit 10 match ip address INSIDE-No-NAT
!
ipv6 access-list FirewallIPv6
remark # Permit DNS responses
permit udp any eq domain any gt 1023
remark # Allow return traffic from outbound TCP sessions
permit tcp any any established
remark # Permit icmp to external interface
permit icmp any host 2001:470::2
deny ipv6 any any
!
ipv6 access-list NetMgmt
deny ipv6 any any
!
control-plane
!
!
line con 0
line aux 0
line vty 0 4
session-timeout 3
access-class 10 in
password MY_PASSWORD
ipv6 access-class NetMgmt in
transport input ssh
line vty 5 16
access-class 10 in
ipv6 access-class NetMgmt in
transport input none
!
end
Here are the assumptions made in the above:
| External WAN interface (where you hook your internet provider’s Ethernet cable) | Interface 2 |
| External WAN interface IP address | DHCP |
| External traffic VLAN (i.e. exposed) | 100 |
| Internal traffic VLAN (i.e. private) | 101 |
| External WAN interface | Eth 2 |
| Internal LAN interfaces | Eth 3 to 9 |
| Internal wired IP network | 192.168.0.0/24 |
| Internal wifi IP network | 192.168.1.0/24 |
| Tunnel interface address (assigned by Tunnel Broker, this is for example only) | 2001:470::2/64 |
| IPv6 address range for wired network (assigned by Tunnel Broker, this is for example only) | 2001:db8:1::/64 |
| IPv4 tunnel destination (chosen by you while setting up Tunnel Broker, this is for example only) | 10.0.0.1 |
| Wifi SSID (you must change this) | MY_WIFI_SSID |
| Wifi WPA2 password (you must change this) | MY_WIFI_PASSWORD |
| Timezone | EST |
| SSH and enable password (you must change this) | MY_PASSWORD |
If you know what you’re doing, you can change any of the above to match your preferences, and of course some of it is assigned by Tunnel Broker to you for your use on the router. Here are a few things that this config does which you may or may not want:
- Interfaces 0 and 1 are not used. There is a reason for this. Interfaces 0 and 1 are routed interfaces while interfaces 2 through 9 are switched. You can NOT bridge from the routed interfaces to the switched interfaces. This means, if at some point, you pick up some more IPv4 addresses from your ISP and wanted to have some external-facing devices, such as your Xbox or a web server, if you were using the routed interfaces you’d have no way to do that because you wouldn’t be able to place the device on the same network as the external interface 0 or 1. What I’m doing in the config instead is defining a VLAN, number 100, as the external VLAN and making port 2 the only member of that VLAN. Then we place the ISP access information on “interface VLAN 100” instead of on the physical interface. Now, if you get another IP from your ISP and want to put your device external, you simply change any of the interfaces from 4 to 9 to “switchport access vlan 100” instead of 101, throw your device on and you’re good to go.
- The WIFI interface is a routed interface in this configuration. It is not bridged to any of the switchports and is not a member of VLAN 101 (your inside VLAN). Additionally, I have put an access control list (ACL) on the wifi interface to explicitly block traffic from the wifi network to your internal wired network (192.168.0.0/24). This means if someone hacks your wifi pass phrase, they still cannot talk to your internal computers, they can only get to the internet. If you do not want this and want your wifi network to be able to talk to your wired network, simply remove “ip access-group WIFI-Restrict in” from the dot11radio0 interface config.
- This config assumes your external IP address is assigned by DHCP. Unfortunately, because of that, there’s also no way for you to enable ICMP replies from your external address, so you won’t be able to ping your IP from remote to test if it’s online unless you were to allow all ICMP in. Right now the ACL drops it.
- The router will only be manageable via SSH from your wired network.
- The router will not be reachable via IPv6 for management.
Now, one final piece. Your wifi network does NOT have IPv6 support because this hardware doesn’t support it on the wifi interfaces. If that is a problem for you, all is not lost. I’m not going to give you the config to do it but it’s very easy if you know at least a little of what all the above config is doing. Here’s what you’d want to do:
- Get rid of the config on the wifi interface and shut it off.
- Define a third VLAN, 102.
- Pick an unused switch port, let’s say 9, and make it an access vlan 102 port.
- Define an interface VLAN 102 and apply the ip address config that had been on the wireless interface.
- In Tunnel Broker, request a routed /48 add-on for your existing /64 they had given you for this network.
- Choose any /64 out of the newly assigned /48 and assign it to the vlan 102 interface.
- Add “ip access-group WIFI-Restrict in” to the vlan 102 interface if you want to keep the wifi folks off your wired network.
- Create a new IPv6 ACL that denies access from your wifi /64 to your 2001:db8:1::/64 wired IPv6 network range, permit to everything else. Add that ACL to the vlan 102 interface as well. That will keep your wifi users IPv6 traffic off the wired network.
- Purchase the cheap-o E3000 router mentioned in the first section of this document, throw DD-WRT on it, turn on IPv6 support, turn off DHCP and everything else, set up wireless and wifi security, set up bridging between port 1 and wifi (i.e. put them on the same VLAN), plug port 1 into your Cisco 1811’s port 9. Wifi users will now use encryption and the SSID of the E3000 device running DD-WRT, but once they’ve authenticated, they’ll get DHCP from the Cisco and use SLAAC to configure their own IPv6 with the Cisco as their default gateway. Now you’ve got IPv6 wifi.
Cisco 1941W Router
Coming soon…